With Website Security becoming an essential element of running a successful online business, we've put together 11 keys steps to improve your Website Security.
Increasing Threat
Over the last couple of years we have a steady increase in the numbers of e-commerce websites being hacked and losing their customer data – including personally Identifiable information (known as PII), credentials (usernames and passwords) and credit card information.
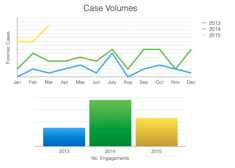
“Steady increase” in hacked online business may not be the right description - in fact this year, our forensic team is forecasting a six-fold increase in the number of forensic investigations on hacked business when compared with our 2013 numbers – although the team did work some massive cases that year.
It’s a nightmare having to face the fact that your business has been ransacked and all the valuable customer data is stolen. Some of the ramifications that you may have to deal with are:
- Stolen Identities – if you have been storing a lot of personally identifiable information, criminals may be able to use that information to steal your customer’s identities – a major problem for your customers.
- Fraud – stolen credit card data is very easily transferred into cash through fraudulent transactions or simply selling the data to another criminal. Most of us have had our credit card numbers stolen – its inconvenient at best, can cause a significant issue as a worst case with cards being cancelled. What does your agreement with your bank say about protecting the card data – will you be held liable for this fraud?
- Reputation – it takes a lot of hard work, long hours a great product and great service to build a strong reputation. A good reputation can quickly be badly tarnished through unhappy customers that work out that your website was not storing their information quickly. It only takes a couple of complaints on social media about unauthorized card transactions to begin impacting your reputation.
11 Steps to Improve your Website Security
Defending your business from digital/cyber attackers is important for the success of your business. The good news is that it can be done reasonably easily. We believe in a “defence in depth” strategy – having multiple layers of defence around your website will give you the best chance of detecting an attack early and defending effectively. Below are 11 steps you can take to improve your website security and reduce the risk of becoming a forensic statistic. You cal also download the infographic here.
1. Update your software.
In recent years, the vast majority of businesses, large and small, are using platforms such as Magento, Drupal, OS Commerce, WordPress, Joomla! and many others. They do so for good reason – these frameworks make the building and maintenance of a highly effective e-commerce business a lot easier than doing a custom or bespoke build. The key with using these platforms is that you need to make sure you are using the most up-to-date version – and that you update your website as soon as a new patch is issued. Huge numbers of websites are hacked daily just because they are using old versions of software on their website. In addition, using a web application firewall ensures that while you may not be lightning quick in rolling out the latest update, the web application firewall will protect your website like a “virtual patch”.
2. Create a custom Admin PathAttackers begin many of their attacks utilizing automated techniques that look for standard configurations on websites to then initiate brute force attacks on username/password combinations. By changing your Admin Path from yourwebsite.com/store/admin to yourwebsite.com/store/alskdj (or whatever you want), the attackers will have to work a lot harder to find your admin page to attack.
3. Passwords
Our forensic manager, James Allman-Talbot, wrote a great article on passwords. We would highly recommend you follow his advice and create a very strong, complex, unique password to access your website admin interface.
Most clients ask us how they are supposed to remember long unique and complex passwords – we would recommend using one of the password managers (LastPass, 1Password, KeePass), which will make your password management a LOT easier and more effective.
Yes, these solutions are not failsafe – LastPass recently announced a security breach. However, they do present a much more effective way to manage the many passwords we all have to use on a daily basis – and if you rotate the password you use for your password manager your risk of having your passwords compromised in one of these password managers is significantly reduced.
4. File Change Monitoring
One of the first signs that a website has been compromised is when files start being introduced, changed or deleted. Unfortunately in the daily management of a busy website, an attacker's small file changes can easily be missed without the technology to monitor for changes.
- Changes made by your web developers = good.
- Changes not made by your web developers = likely attacker activity.
Monitoring the changes taking place on your website is an essential step in detecting malicious activity and can be done very effectively.
5. Malware
Malware stands for “MALicious softWARE” – a term for all sorts of software used for criminal activity. Of all the websites we assist following a breach, around 90% have had malware introduced into their website to:
- Provide a back door for later access.
- Load up other malicious software.
- Enable stealthy reconnaissance.
- Provide interactive access for the attackers.
- Steal credit card data.
- Steal personal data.
- Or all of the above…
Some malware is detectable by doing an external scan (have a look at our free Magento and WordPress scanners) however, most of the malware we have encountered is well hidden within a website – evading detection by even some of the most vigilant web admins.
We recommend daily checks using an advanced malware detection solution as a highly effective defence against malware attacks.
6. Manage your users
If you have multiple logins to your website, this applies to you. It is very important that you:
- know each user; and
- assign the appropriate permissions to them for their role within your business.
As an example, if you need to grant escalated privileges to a user momentarily, make sure that you reduce their privileges once they have completed their work.
Do not allow sharing of accounts – you need to make sure you can understand exactly who is doing what on your website. Using shared accounts means that if one of the “sharers” makes a change, how do you know who was responsible?
Monitoring for unusual user activity will alert you to possible account compromise.
7. Monitoring Website Activity
Monitoring, reviewing and storing a log of all activity on your website is key to detecting attacks and enabling you to defend yourself. You need to be analysing this data (at least) daily to identify threats – better to be alerted in near-real-time. If you handle credit/debit card transactions, you need to store at least 12 months of your security log data to meet Payment Card Industry Data Security Standard (PCI DSS) requirements.
8. Monitor for Unprotected Credit Cardholder Data
Most e-commerce websites are correctly set up to handle transaction data securely – often by using a secure payment service from a payment service provider. However, considering that payment cardholder data is highly valuable to a criminal, many websites continue to fall victim to payment cardholder data theft.
The attacks usually involve malware, changes to a website and unusual system behavior – all of which should be detected with other layers of detection and defence, such as those highlighted above. But if the attackers manage to evade detection to the point where they are able to extract transaction data, usually they will store that data in a file somewhere on your website for later harvesting. More often than not this payment card data awaiting extraction is not encrypted.
A regular “PAN scan” of the website’s file system and databases for unprotected credit cardholder data will identify these files ready for exfiltration and alert you to the issue.
9. Use an Advanced Web Application Firewall
Our research in carrying out forensic investigations on online businesses over the last decade has shown that in over 95% of all hacked e-Commerce businesses investigated by our team over a 10 year period have fallen victim to one of these three major threats:
- SQL Injection
- Application Vulnerability Exploits
- Injected code (malware)
A properly configured and managed Web Application Firewall will protect your website against these attacks. Not only that, a Web Application Firewall will provide a website with “virtual patching” when a zero day vulnerability is released. This protection will buy a web admin time to test the patch and then update the system in his/her own time, knowing that the website is protected.
- 10. Test and Test Again
The Internet is a dynamic, evolving entity and your website won’t remain static either. This means it requires regular security testing to keep on top of any new vulnerabilities that can develop.
There are two recommended approaches for security testing:
- Vulnerability scanning – this is (generally) a non-intrusive method that involves sending traffic, queries and specific requests to the website to test if vulnerabilities exist. This should be carried out at least once per quarter, is cheap and can be automated.
- Penetration testing – this is a more in-depth testing process than vulnerability scanning, carried out by a specialist company who mimics or emulates the behaviour of an attacker. It’s recommended that penetration testing is carried out at least annually, and while it’s more expensive than vulnerability scanning, its overall effectiveness makes it well worth the investment, even for small businesses.
11. Find an experienced security partner you can rely on
One of the greatest challenges we see is online businesses trying to do everything themselves. Generally, we all have our speciality skills that we employ in our day to day business – most of us understand the markets we work in and know what it takes to compete effectively.
When it comes to security of your business, understanding the threats and the skills of your adversaries is crucially important in defining your defence strategy.
The level of skill that we see being employed by attackers on a daily basis, indicates that they are specialists employing their skills to steal data from less skilled victims.
An analogy we’ve used recently to illustrate this is comparing the security skills in the average online business with those of an average attacker is like comparing the skills of St Ives under 10’s football team with Manchester United.
There is a significant skills mismatch across the industry – there are not that many skilled security specialists available for hire and those that are available don’t come cheap.
So to put the odds more in favour of the online business, we would recommend:
- finding the right technologies
- implementing effective procedures; and
- finding a security specialist partner you trust to support your business.
While this list is not exhaustive and will not guarantee that your website will not get hacked, these are a few of the key steps we would recommend to form an effective “Defence in Depth” strategy for your website and will ensure that you are able to detect/repel the vast majority of attacks.
How can we help you?
Firstly, we are security specialists.
Secondly, we have a solution called FGX-Web that protects websites with:
- File Change Monitoring - FGX-Web has file change monitoring built in to alert our clients on any changesbeing made to their website. With granular controls on monitoring, you can be alerted on anything that is suspicious.

- Security Event Log Monitoring - FGX-Web provides automated log collection, analysis and alerting as a standard part of the solution, making this a lot easier to manage. We also store your logs for you to access later if needed.
- Payment Cardholder Data Scanning (PAN scanning) – FGX-Web performs daily checks for unprotected payment cardholder data across your website filesystem and database.
- Advanced Web Application Firewall – FGX-Web includes a fully managed, advanced web application firewall to protect your website from malicious attacks.
- Daily Malware Detection – including our Basehunter technology designed to detect the hard to find malware that usually evades most commercial malware detection tools.
- Unlimited Support – if you have a security problem with your website, our team are here to help get your business back up.
FGX-Web is a unique solution that we’ve built to help online businesses defend themselves. You can find out more here:
Subscribe to our Blog
TAGS:
Web Security

Benjamin Hosack
Benj Hosack is a Director and co-Founder of Foregenix Limited. Foregenix is a specialist information security business delivering services in Forensics, PCI DSS, PCI P2PE, PA-DSS and information security solutions within the Payment Card Industry. Our technologies are designed to simplify security and PCI Compliance. Specialties: Cardholder Data Discovery - defining and reducing PCI DSS Scope / PA-DSS / PCI DSS / P2PE / Account Data Compromise Investigations. We are specialists in the Payment Card Industry and work with all types of companies in the payment chain (Acquiring banks, Processors, hosting providers, web designers, merchants, systems integrators etc).
See All Articles