To defend against most online threats, you need to invest heavily in third party software to keep your eCommerce environment on lock down. You can have the best security systems in the world, but one well placed social engineering attack can undo all of your hard work and render your investment useless. Being aware of what social engineering is and the potential impact it can have on your business is critical to keeping your customers safe.
What Is Social Engineering and How Can It Threaten Your Business?
According to a 2016 report from Agari, 60% of security leaders surveyed were the victim of a targeted social engineering attack, with 65% of those who were attacked say that employee’s credentials were lost as a result. Financial accounts were accessed in 17% of attacks.
What is a social engineering attack?
Social engineering is an attack method that that utilises deception and human interaction to obtain information or compromise a business’s computer system. These attacks commonly manifest themselves in the form of targeted phishing emails. A report from PhishMe from 2016 attributed 91% of breaches to a successful email phishing campaign. You might be wondering how that’s possible; but phishing emails are no longer poorly spelt messages offering you millions of Pounds/Dollars from a Ugandan prince.
Phishing emails can be well constructed, seemingly legitimate communications from big companies. It’s easier than you think to fall into the trap of clicking a malicious link or downloading a fraudulent attachment. Unlike spear-phishing emails, regular phishing emails are usually sent out en-masse
Attackers will make use of all kinds of tactics to get you to fall into their traps. In 2017 following hurricane Harvey, faux emails were circulating asking people to donate money to aid groups. Of course, it was in fact a dud link, loaded with malware.
Here’s an example of a phishing email I received last year:
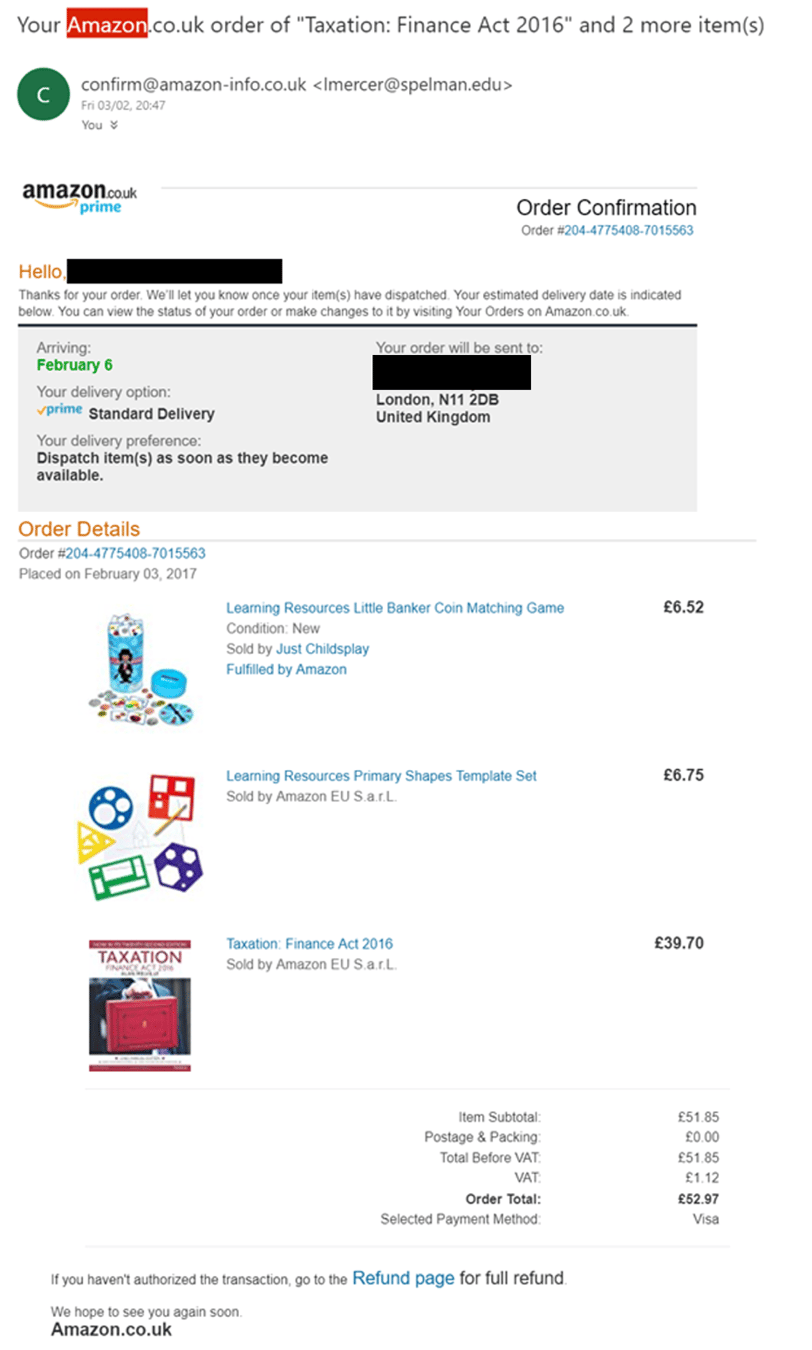
Looks pretty legitimate, right? If you’ve shopped at Amazon before, you’ll recognise this email as the automated communication that’s sent out when you purchase an item. However, I hadn’t purchased anything. The attacker had set this up to trick me into thinking my account had been used fraudulently to purchase goods and have them delivered to an address in London.
Let’s take a look at it in a bit more detail:
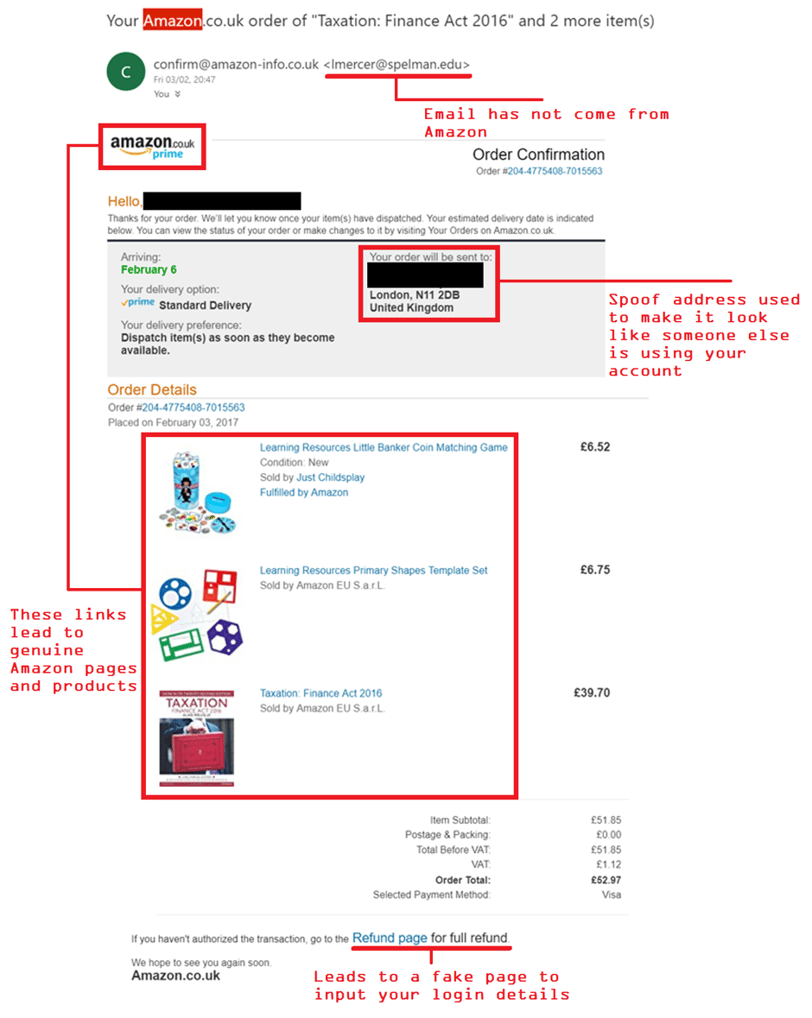
Without casting a sceptical eye over it, you might find yourself taking the information at face value. This is of course what the attackers want you to do. Using the fear of a possible fraudulent transaction, they have preyed on the fact that you would be likely to click the ‘go to the refund page’ link at the bottom of the email. Clicking the link leads to a malicious webpage asking you to input your login details. Hovering your mouse over the link will reveal its destination address, in this way you’re able to tell that it’s not leading to a legitimate Amazon webpage.
Free Webscan
In today’s online climate, you shouldn’t immediately trust anything you’re sent. After all, having CCTV, armed security, a guard dog and laser guided missiles to protect your house mean nothing if you let the pizza delivery guy in without questioning him first.

But what’s a spear phishing email?
Spear phishing works slightly differently to conventional phishing emails, but the principals of deception remain the same. Spear phishing involves targeting a specific individual or business. They will use individually designed techniques in an attempt to personalise messages and websites. In this way, high ranking employees such as executives can become victims at the hands of emails they thought were safe.
Whereas regular phishing emails are usually sent under the guise of a big company such as PayPal or Amazon, spear phishing emails are likely to appear to be from someone within their own company. Generally speaking the email will look like it’s come from someone in a position of authority. In this way they’re able to manipulate the trust employers share with employees, resulting in a successful attack.
Spending time gathering information about the intended target will lead to a more personalised attack. Being able to use someone’s name or job title will make the source appear more trustworthy and legitimate.
Here are some tips to avoiding phishing attacks, drawn from US-CERT:
- Be suspicious of unsolicited phone calls, visits or email messages from individuals asking about employees or other internal information. If an unknown individual claims to be from a legitimate organisation, try to verify his or her identity directly with the company.
- Do not provide personal information or information about your organisation, including structure or networks unless you are certain of a persons authority to have that information.
- Do not reveal personal or financial information in emails, and do not respond to email solicitations for this information. This includes links sent in emails.
- Pay attention to the URL of a website. Malicious websites may look identical to a legitimate site, but the URL may use a variation in spelling or a different domain name.
- If you are unsure whether an email is legitimate, try to verify it by contacting the company directly.
- Install and maintain anti-virus software, firewalls, and email filters to reduce some of this malicious traffic.
- Take advantage of any anti-phishing features offered by your email client and web browser.
Scepticism is the name of the game when it comes to keeping yourself and your business safe from phishing attacks. Trust nobody that asks you to click a link unless you’re 100% sure it’s legit. If you think your system/website may have been compromised by malware, contact us for help.
VIEW CYBER THREAT DETECTION