This two-part series is focused on reducing the impact of a breach through early detection. In part one we looked at the change in mindset from purely preventative measures, to implementing effective detection methods within your environment; and the positive impact that this could have. In this article we will look at bridging the gap between the initial point of intrusion and instigation of an effective incident response plan.
80% of businesses do not have an incident response plan, 15% have a documented plan but lack the foundation to provide an efficient or effective response, leaving only 5% [1] of business with an actionable incident response plan in place. In this, the second part of our IR series we are going to look at the need for an effective and functional Incident Response plan.
We are entering an era of criminality where ransomware and card data theft are being seen on a regular basis across all industries; from health to manufacturing and eCommerce to retail. Cybercrime is considered a high profit and low risk criminal activity, with losses to businesses mounting into the billions annually.
As times have changed, it’s become a matter of when an organisation will be compromised, not if. Incident response planning is critical for all organisations, but what does this mean and what makes a plan actionable? First and foremost, an incident response plan requires a formal, documented, process. To be effective, it must be signed up to by the entire organisation from the top executives/board level, right the way through to the lower levels of the company.
A plan that is not signed up to by the company executives and not widely distributed throughout the firm cannot be expected to provide an effective response in the time of need. To be an effective incident response plan, it should be a written set of principles, rules, or practices, specific to an organisation. It must detail user security and more importantly, incident identification.
We recommend these 10 tips for an effective Incident Response plan:
- Assign Executive Responsibility for plan creation, implementation and maintenance
- Identify all assets of the business and potential threats to those assets
- Define an Incident Response Team
- Identify and establish a service contact with an Incident Response Partner
- Establish contact with local Law Enforcement
- Define a decision-making process within your internal IR team
- Document the plan and share across the business
- Create a communication strategy
- Create a legal strategy
- Test your plan
The incident response document should be the keystone of any organisation, providing guidance to it's users through all phases of an incident response. It should include specifics, like how to handle an incident, and prioritise responses based on organisational impact. For example, IT support receive a call from a user saying their workstation is acting strangely, whilst at the same time someone reports finding a USB thumb drive within a public area. At which stage should these incidents be declared as a security matter and the incident response plan become invoked?
Communication planning is one of the most overlooked areas, with little or no consideration made as to who to contact, and when. Consideration should be given to all forms of communication, from initial reporting and escalation of an incident, through to notifying senior members and the remainder of the company. External communication must also be taken into account, who will be responsible for its delivery, how much will they be prepared to say and what will be used to “fill the gap” while the details are being sought?
A strategy must also be implemented for making an incident public or responding to external interest (such as the media, or customers). Any organisation must be sure to avoid single points of failure within the communication plan. Naming single individuals looks fine on paper, but in the heat of an incident, who should be notified when the named individual is unavailable?

It’s vital for an effective response to any incident to assign roles and responsibilities to individuals within the organisation. These should be predetermined within the document, and those involved must be made fully aware of their requirements. In order for the incident response to be effective, everyone must have a clear idea of what exactly is expected of them. Consideration should also be made to role deputies or substitutes to cover the eventuality that a named individual with a key role is not available.
During an incident is not the time to be deciding what roles individuals should perform, or whether individuals have the correct skill set to perform the role. As part of the role assigning process, a Security Incident Response Team (SIRT) could be developed and listed within the plan. Creating a team of correctly trained and skilled employees that can be brought together, each knowing their role and responsibility as part of the incident response; could greatly improve the effectiveness and efficiency of the response.
This is not just a team of technical persons, but should include those from HR, legal, marketing and PR, covering all elements of the planned response. Once again single points of failure must be avoided, with deputies nominated for principle roles.
There are great benefits to having an effective and efficient incident response plan:
- A reduction in discovery time and ultimately a reduction in the impact to the organisation.
- An early and effective investigation with efficient evidence capture, which may include early engagement with third-parties such as specialist Incident Response companies or Law Enforcement.
- A swift closure of the incident and return to business as usual.
Having an incident response plan is the first step to improvement, but no plan will survive first contact with the enemy unless it is tested and rehearsed – making it Incident Ready. It is also important to define and understand chains of command and authority. Mixed messages and wavering decisions can easily arise within environments that suffer from the “too many cooks” issue. Information sharing is key and specialist knowledge invaluable but a single conductor that can make rapid (but not hasty) informed decisions is vital.
A typical incident from the point of view of an organisation initially consists of business as usual, then at some point, an attacker breaches the environment. There is then a period where the victim is unaware that an attacker has breached their environment; before the incident is detected.
The security elements protecting any environment predominately focus on the business as usual phase of the victims time line, looking to identify the early signs of an attack, during the reconnaissance and initial attack stages, or where possible prevent the attack altogether. It’s common for incident response plans to not be called into action until after the attacker has gained access to the environment, potentially begun to cash out, and the incident is detected.
The above illustration identifies a potentially large gap between the security controls in place and the incident response plan being initiated. It’s this area where effort should be made to improve incident identification and detection within the incident response plan. We cover this section in more detail in part 1 of this series. The aim for any organisation should be to invoke their incident response plan as close to the point of compromise or potential compromise as possible.
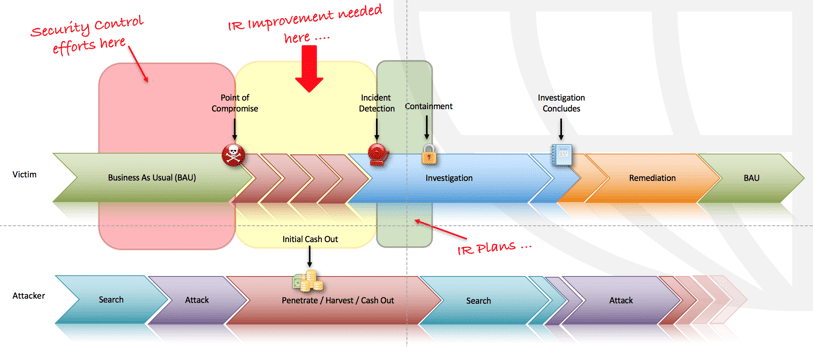
It’s the window between the point of compromise and the incident detection that causes the most impact on a business. In cases where card data is compromised, this window is often reduced through the use of third-parties (such as Payment Brands, Issuers, and Acquirers) of whom contribute to the detection of a security incident.
For breached organisations where other valuable data such as intellectual, or commercial property is at risk, the reliance of detection lies solely with the organisation. Therefore, the window between compromise and detection can be exponential.
The most advantageous way to improve your incident response plan and shift it to an effective process ready for any incident, is regular testing. It’s only through testing that the effectiveness of your plan can be demonstrated; honed where needed, and those with assigned roles and responsibilities can truly learn and experience.
Your plan should be tested and stressed in a variety of ways, including table top walkthroughs, focused penetration tests, full on red team attacks and even uncontrolled penetrations tests, to ensure that your plan is truly Incident Ready!
In conclusion to this series on Incident Response, by utilising products such as Serengeti, or FGX-Web, coupled with our managed service, we can reduce detection time potentially down to a number of hours instead of months. It allows you to get a chaotic situation under control, potentially before the intruder has the opportunity to do any lasting damage; so you can quickly get back to running your business.
We also have experience and expertise that can be used to assist you in developing, implementing and ultimately testing an effective and efficient incident response plan that meets the individual needs of your network or business. For more information on Incident Response, Incident Detection or any of our other services please contact us!
View Incident Readiness Services
[1]Figures are general estimates based on Foregenix' own assessment.
Subscribe to our Blog

Benjamin Hosack
Benj Hosack is a Director and co-Founder of Foregenix Limited. Foregenix is a specialist information security business delivering services in Forensics, PCI DSS, PCI P2PE, PA-DSS and information security solutions within the Payment Card Industry. Our technologies are designed to simplify security and PCI Compliance. Specialties: Cardholder Data Discovery - defining and reducing PCI DSS Scope / PA-DSS / PCI DSS / P2PE / Account Data Compromise Investigations. We are specialists in the Payment Card Industry and work with all types of companies in the payment chain (Acquiring banks, Processors, hosting providers, web designers, merchants, systems integrators etc).
See All Articles