The Foregenix DFIR team has discovered what is believed to be an unreported piece of malware which has recently been used to target insecure eCommerce websites processing through Stripe, running on the Magento framework.
The Malware
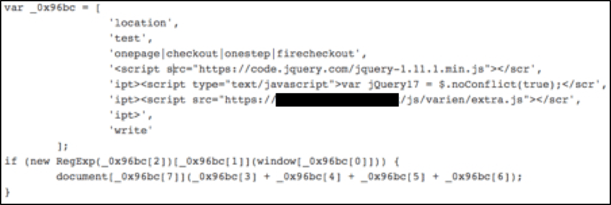
Dubbed ‘Ajax Harvester’ by analysts, the malware is a piece of JavaScript which, when inserted into a compromised site, waits until a Magento payment page is visited. It specifically looks for payment pages using the One Page, CheckoutSuite, One Step Checkout and Fire Checkout page titles, as shown below.
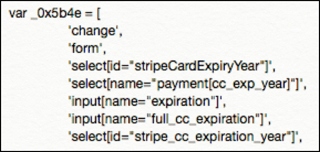
If a payment page is identified, it calls a further JavaScript (in this instance named ‘extra.js’) which searches for input fields specifically related to the ‘stripe.js’ Magento payment integration. Some of the malicious code is shown below.
Although the malware is not unique in its functionality it does mean users could have their credit card data stolen even before they have pressed the checkout button. Rather than harvesting code to a local harvest file for later retrieval by the attacker, it immediately posts the data using a JQuery AJAX function to an external server controlled by the attacker as soon as values have been entered into an input field.
What makes the malware distinct is the fact that it is directly targeting the Stripe.js code for Magento.
Prevention
This attack is only possible when a website is insecure - just to be clear, while this attack focuses on the Stripe.js integration for Magento, it can only take place when the website itself has been hacked. Preventing this attack therefore requires a website administrator/web developer to keep the website secure. Here's an article we recently wrote on Securing Your Magento Website.
Detection
In order to detect this malware on your website, you'll need an internal scan of your environment that looks for key indicators of compromise.
You can detect these by using a free Website Health Check service from the Foregenix team.