PCI DSS requirement 10 specifies that organisations must track and monitor all access to network resources and cardholder data. In this blog I seek to outline and explain PCI DSS requirement 10.
PCI DSS Requirement 10: A Guide to Logging and Monitoring
Organisations must ensure that logging is enabled for all system components which means for all network devices, servers, end-points and application within the PCI DSS scope. Logging must include all access to system components and is linked to individual user accounts. Further, logs must be retained for at least one year with three months immediately available for analysis.
Each audit trail (or log) must at least record the following informational items as outlined in Figure 1 below. For all system components and for each event the log entry must include at least the below list.
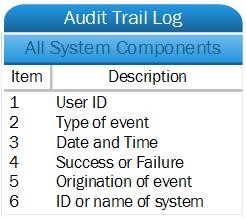
Figure 1 – Minimum information to be logged in each log entry.
Including logging the minimum informational items for each log, the logging process should allow for the following events to be reconstructed as outlined in Figure 2 below.
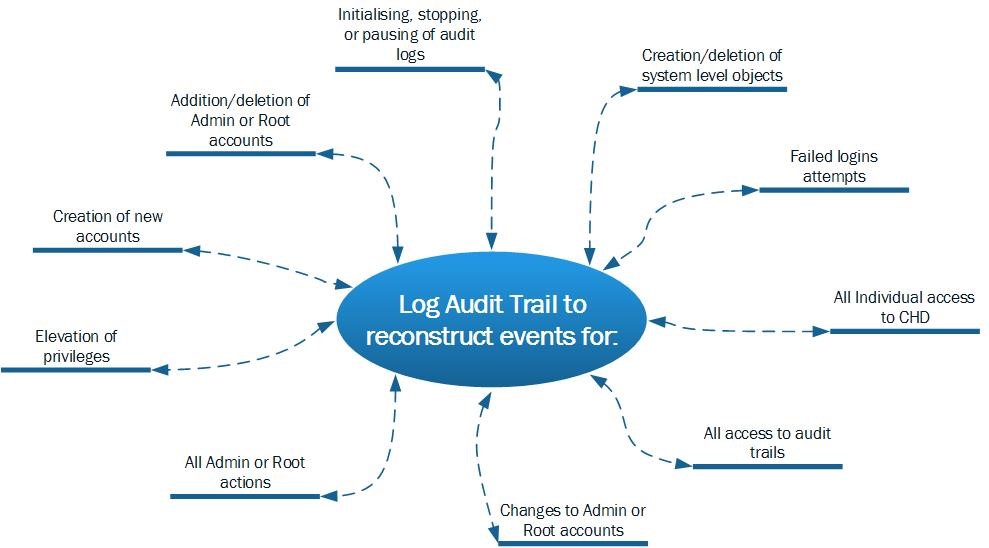
Figure 2 – Events to be reconstructed from logs
There must be procedures in place to ensure that logs are reviewed periodically and security events identified and investigated appropriately. The following must be reviewed daily:
- All security events
- Logs for all systems that store, process or transmit CHD and systems that could impact security of CHD
- Logs of all critical systems
- Logs of all security servers and systems, e.g. firewalls, IDS/IPS, Authentication Servers, E-Commerce redirection servers, etc.
Logs for all other systems must be reviewed periodically based on the annual risk assessment and the organisation’s policies. The procedures must include steps to ensure that all exceptions and anomalies identified during the review process are followed up. These procedures must be documented, in use and known to all affected personnel in the organisation.
Requirement 10 also specifies that critical systems must have correct and consistent time which includes log servers. Time data must be protected to prohibit unauthorised access to time data and unauthorised medication of time settings. This requirement also specifies that time settings are received from industry-accepted time sources.
Having outlined the above, consideration must also be given to ensure all logs are secured so that they cannot be altered. Logs must only be accessed on a need to know basis and protected from unauthorised modifications. All logs must be backed-up to a centralised log server promptly. Logs from external-facing systems must be secured onto a centralised internal log server. Finally, the organisation need to use file integrity monitoring (FIM) to monitor changes to logs.
If you'd like any further help regarding PCI DSS requirements, please contact us using the form below.