Magento Security: The Forensic Team at Foregenix has identified a number of cases concerning the same method of Brute Force attack.
Attackers were able to gain access to the Magento Connect Manager of multiple Magento websites, through Brute Force Attack, due to a combination of weak passwords, open access to the website’s Magento extension download page (www./downloader/.cache/community), and open access to the Magento Connect Manager login page itself (www./downloader/index.php), neither of which should be publicly available.
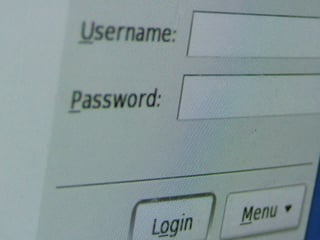 The attackers were then able to upload a genuine, non-malicious extension by Magpleasure which allows total editing of Magento Files straight from the administration panel - granting the hacker full control of the Magento environment.
The attackers were then able to upload a genuine, non-malicious extension by Magpleasure which allows total editing of Magento Files straight from the administration panel - granting the hacker full control of the Magento environment.
This was then followed by two webshells being uploaded to the website, allowing an attacker to add/edit/delete files within the web root.
Detection
We have outlined how you can detect this malware yourself in a technical Whitepaper which you can download using the button below.

Alternatively, we are offering a free 7 day trial of Vngo to allow you to scan your website internally for these webshells.