We have come across Manage Engine EventLog installations a few times in our penetration tests at Foregenix, and have identified different vulnerabilities in our attempts to compromise it. In most situations a default guest account was left open and becomes a focus point as we attempt to use it to elevate privileges or otherwise influence the profiles behaviour to our advantage. These attempts resulted in the following vulnerabilities being discovered and reported to the vendor. While the installations encountered during the engagements may not be running an up-to-date version of the ManageEngine EventLog software we validated whether the vulnerabilities still exist on the latest version as of the time of reporting them to the Vendor.
“EventLog Analyzer provides the most cost-effective Security Information and Event Management (SIEM) software on the market. Using this Log Analyzer software, organizations can automate the entire process of managing terabytes of machine generated logs by collecting, analyzing, correlating, searching, reporting, and archiving from one central location. This event log analyzer software helps to monitor file integrity, conduct log forensics analysis, monitor privileged users and comply to different compliance regulatory bodies by intelligently analyzing your logs and instantly generating a variety of reports like user activity reports, historical trend reports, and more [1].“ The latest version of ManageEngine EventLog has been merged with ADAudit Plus into a new offering called ManageEngine Log360 and is a new entrant to the Gartner Magic Quadrant for SIEM in 2016, being placed in the Niche segment.
Reset of any user account’s password
A vulnerability has been identified in ManageEngine EventLog 10.7 SIEM application where any user can change the password as well as email address of any other user on that installation. When a restricted user logs into the application, he is greeted with a screen containing only the offered functionality based on his profile and all other options are disabled and “greyed out”. An option that is available to the user is the ability to change their password and registered email address.
From a user interface level this is accomplished by calling the defined JavaScript function editNonAdminSettings('2') where 2 corresponds to the userid of the logged on user, in this case it maps to guest. A malicious individual can change 2 to 1 and be allowed to change the admin user's password. The same functionality seems to be exposed when calling the editNonAdmin('X') JavaScript function however nothing is presented to the user.
This vulnerability has been fixed in ManageEngine EventLog Analyzer 11.0
Guest user self-promotion to the Administrators group
A while ago (04/03/2015) Foregenix identified a vulnerability in the – then - latest ManageEngine EventLog 10.5 that allowed a low privileged user, guest for example, to self-promote himself to an Administrator by posting data to the following URL.
http://127.0.0.1:8400/event/index2.do?url=usermgmt&productName=eventlog&helpP=userMGMT&tab=system
This interaction was triggered by
- An authorisation issue that allowed a restricted user to access the user management section, much like [2] while he should have been denied to do so
- Executing the
individualRole("2");JavaScript function where 2 corresponds to theuseridof the logged on user, in this case it maps toguest. A malicious individual can use that JavaScript function in order to display theAdd to Groupdialog that can be used to assign the desired username to the desired group.
ManageEngine was contacted about the vulnerability and proceeded to fix it. ManageEngine appeared to have resolved the issue in its 10.6 - Build 10600, as it specifically stated in its release notes for that version “Guest user promotion as Admin by accessing user management page has been fixed”. Foregenix did not test the validity of the patch however. The patch attempted to address the issue by firstly disallowing a restricted user to access the user management screen and then with an additional check when the data were actually being POSTed back to the application that returned a 403 Forbidden HTTP code.
Foregenix identified that the patch provided was ineffective. An attacker can still POST a request that can promote himself to an Administrator level. When a guest user calls that on a patched version of the ManageEngine EventLog application he is met with an HTTP/1.1 403 Forbidden response, however for some reason the request is acted upon and the guest user is still granted admin access. The following request can be used as a proof of concept:
POST http://127.0.0.1:8400/event/index2.do?url=usermgmt&productName=eventlog&helpP=userMGMT&tab=system HTTP/1.1
Proxy-Connection: keep-alive
Content-Length: 293
...
domainId=&roleId=&password=&email=aaaadmin%40adventnet.com&addField=false&userName=admin&userID=1&changePassword=false&domainName=&isPlugin=false&alpha=&userIds=2&roleName=Administrator&selDevices=&doAction=assignRole&productName=eventlog&licType=Prem&next=¤tUserId=2&isAdminServer=false
The highlighted 2 in the code snippet above corresponds to the guest user.
This vulnerability has subsequently been fixed in ManageEngine EventLog Analyzer 10.8.
SQL Injection
Foregenix identified that most – if not all – of the forms used by the application interact with the database either for retrieval or manipulation of the stored data. Within the time constraints of the engagements performed by Foregenix identified two (2) places where a user can easily inject his own SQL statements into the application; however, many more may still exist. The specific places are:
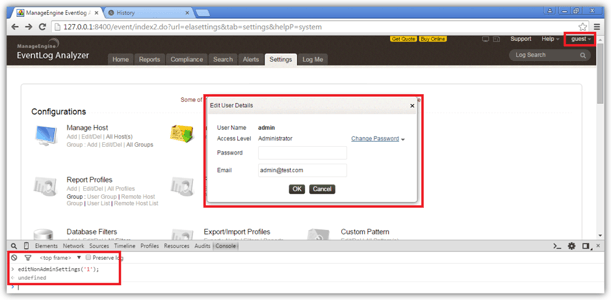
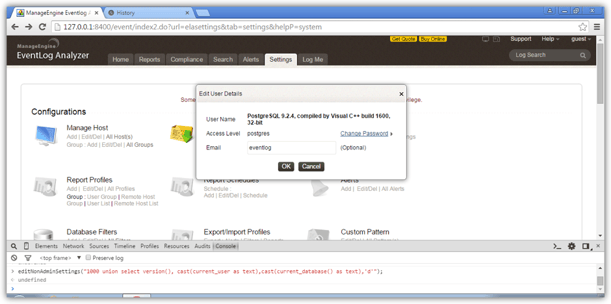
Administer your own account, accessible through Settings → Account Settings → Administer your account and via calling the JavaScript function editNonAdminSettings("1000 union select version(), cast(current_user as text),cast(current_database() as text),'d'");
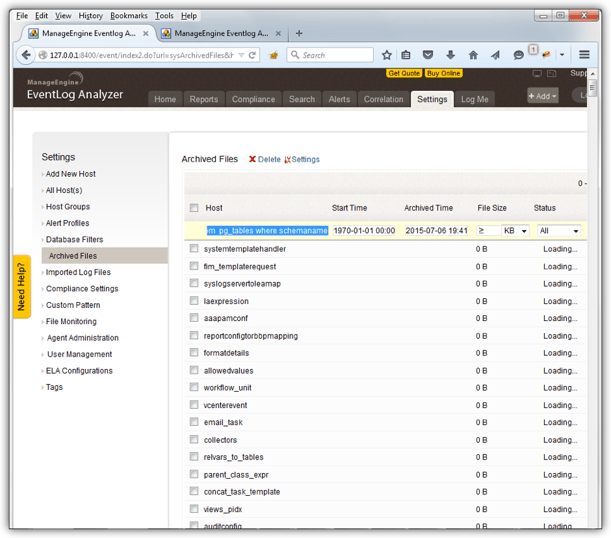
Archived Files, accessible through Settings → Archived files using 0' then '1' else 1=1 end union select lower(tablename) as tn, 1, 1, 'b', null, null, 0, 1, 'c', 'd', 'e' from pg_tables where schemaname='public'—- as a Host filter name.
ManageEngine EventLog Analyzer 11.0 build #11005 includes a fix for both of these vulnerabilities in its release notes. . Foregenix identified that only the Administer your own account function was fixed while in the Archived Files functionality the underlying SQL query was changed to make the initial payload we provided ineffective. Foregenix further contacted Manage Engine about this vulnerability and a fix was eventually pushed out in version ManageEngine EventLog Analyzer 11.3.
Cross-site scripting on the Login page
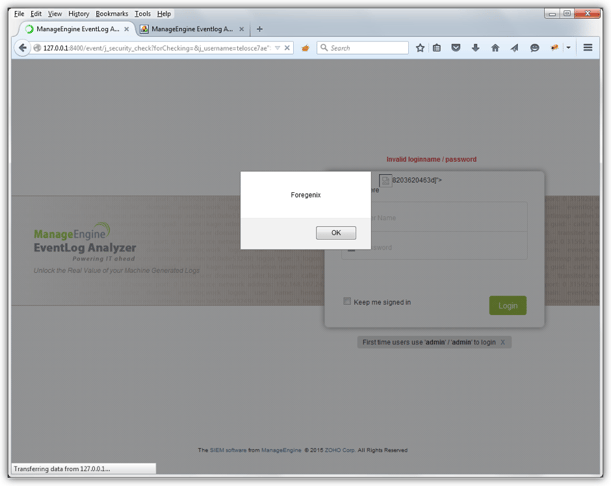
Foregenix also identified that it is possible to inject code into the applications login page by taking advantage of error handlers when loading an image. The following URL can be used to achieve that:
http://127.0.0.1:8400/event/j_security_check?forChecking=&j_username=telosce7ae%22%3E%3Cimg%20src%3da%20onerror%3dalert%28%22Foregenix%22%29%3E8203620463d&j_password=test&domains=Local+Authentication%0D%0A&loginButton=Login&optionValue=hide
The contents of the j_username parameter is the culprit in this case. The example above can be URL decoded to the following:
telosce7ae"><img src=a onerror=alert("Foregenix")>8203620463d
A couple of things are happening above:
telosce7ae">gracefully terminates whatever contents are being input on the username filed of the login form and<img src=a onerror=alert("Foregenix")>introduces a new image HTML element on the resulting web page that instructs the browser to load a new image named a and if it does not find it, that is where theonerrordirective kicks in, execute whatever JavaScript is included in there.
Note: You may have to disable any XSS protections in your browser for the attack to become apparent.
This vulnerability has also been fixed in ManageEngine EventLog Analyzer 11.0 build #11005
Password unmasking in the Database access console
ManageEngine EventLog saves all the application’s information within a PostgreSQL database (by default). It also offers its Administrator users a lightweight and restricted database client in the form of a browser window so they can query its database and retrieve the results back. This is available at http://<IPADDRESS>:8400/event/runQuery.do. ManageEngine imposes a control where if any data stored in database column named password they are protected from display and its contents are replaced by asterisks. Foregenix also identified that this happens at the application layer rather than the recommended situation, to have the data masked at the database layer.
As such, the instruction below returns the data in the second panel:
|
select username, password from hostdetails limit 10 |
|
USERNAME PASSWORD Admin ******** |
This control can be trivially bypassed by tricking the application into believing that the column name is not password but something else. This can be accomplished in a couple of ways, namely using the select column_name as another_name valid SQL directive or using column/value concatenation at the query level such as select ‘’||password||‘’ SQL directive.
So with one of these minor alterations, we end up with the following situation:
|
select username, password as ppp from hostdetails limit 10 |
|
USERNAME PPP Admin 3a8724f70b0b0f77 |
and similarly….
|
select username, ''||password||'' from hostdetails limit 10 |
|
USERNAME PPP Admin 3a8724f70b0b0f77 |
It was made clear through our correspondence with the vendor when we reported this vulnerability that ManageEngine does not consider this a vulnerability for two reasons:
- The password is in encrypted form and
- This function is only available to users belonging to the Administrators group.
We refute their position, and continue to consider this a vulnerability, specifically regarding point 1 above, while the password is indeed in an encrypted form, we have identified that
- in, at least the highlighted case above, this is a reversible encryption since this is the password the ManageEngine EventLog uses to connect to other servers and retrieve their logs, and
- ManageEngine EventLog uses a global key to encrypt that data across all installations thus significantly increasing the risk of someone breaking that encryption.
Regarding point 2 above, restricted to Administrators only, this is only the case if you are running ManageEngine EventLog 10.7 and above since in all prior versions an authorisation issue existed that allowed a user to directly call the database console and it would happily be served to him [2]. Actually, someone beat us to reporting the vulnerabilities in [2] to ManageEngine.
References:
Subscribe to our Blog
TAGS:
Penetration Testing

Benjamin Hosack
Benj Hosack is a Director and co-Founder of Foregenix Limited. Foregenix is a specialist information security business delivering services in Forensics, PCI DSS, PCI P2PE, PA-DSS and information security solutions within the Payment Card Industry. Our technologies are designed to simplify security and PCI Compliance. Specialties: Cardholder Data Discovery - defining and reducing PCI DSS Scope / PA-DSS / PCI DSS / P2PE / Account Data Compromise Investigations. We are specialists in the Payment Card Industry and work with all types of companies in the payment chain (Acquiring banks, Processors, hosting providers, web designers, merchants, systems integrators etc).
See All Articles