We’re fast approaching the middle of 2019, and already we’ve seen numerous announcements of major data compromises involving millions of personal data records being stolen, including:
- Email addresses & passwords
- Passport numbers
- Social security numbers
- Banking information & credit card data
While the largest breaches catch our attention and have done a lot to raise awareness to the threat these criminals pose to our society, what is often less well reported, and therefore, less well understood, is how the smaller end of the business world is being targeted. As an example, we rarely hear about the thousands of successful small to medium eCommerce websites that have been hacked, and are quietly leaking all their customer payment data to criminals every day.
As an active PCI Forensic Investigator, we assist a considerable number of hacked businesses to regain control of their businesses after criminals have ransacked them. The vast majority of these organisations are small, local businesses who never thought that they would be a target for criminals.
"The vast majority organisations we investigate are small, local business who never thought they'd be a target for criminals."
Alongside our Digital Forensics and Incident Response (DFIR) work, we’re also keen innovators and have released a number of solutions to address key issues our forensic team see in the “wild”. One of the most widely used solutions we’ve produced is our Website Security solution, WebScan. It is a free scanner that tells website owners if their website is compromised or at risk of being compromised, providing them guidance on the various issues we see.
Foregenix Global WebScan Statistics
We monitor the security status of nearly 9 million websites around the world and regularly release statistical data to showcase the challenge that we as an industry are facing in trying to combat criminals with the skills and intent to cause significant damage to the vast majority of small to medium sized online businesses around the world.
Our Global website statistics as of May 2019 show that:
- Over half a million websites scanned are considered “HIGH RISK”.
- Over 1,700 were identified as hacked with payment card harvesting malware stealing their customer data.
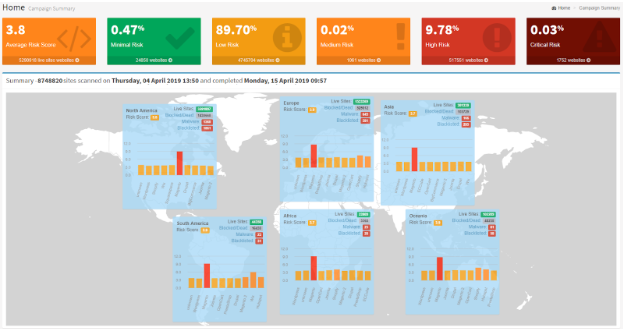
While the hacked percentage may seem low, please bear in mind that we monitor and track nearly 9 million websites. Then consider that the average cost of a breach (according to Vantiv) is $117,000, the potential collective liability across the websites that we know have confirmed malware harvesting their customer data is over $200 million.
When we drilled down into the data, it became clear very quickly that Magento is still rated as the most targeted platform, with the majority of the compromised websites being Magento websites.
Magento - Most Targeted Platform
Global Magento Statistics:
- 86.5% of over 200,000 Magento websites are considered “HIGH RISK”.
- >906 websites are currently hacked with payment card data harvesting malware stealing their customer data.
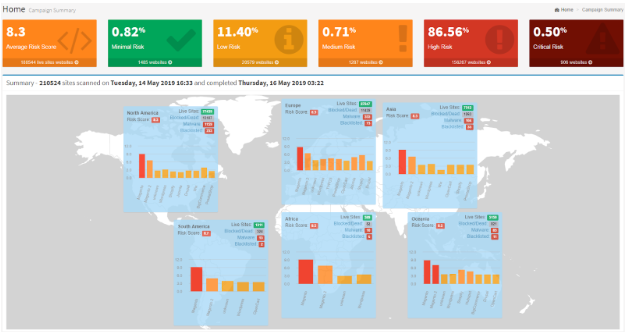
The hacked sites are most likely completely unaware at this point that they have been hacked and are having customer data stolen.
On average (based on Foregenix forensic statistics), the websites are compromised for 5.5 months before they are notified (most common situation) or they detect something amiss (far less common). At this point the criminals have stolen a great deal of data and have likely started to execute fraudulent transactions elsewhere on the stolen payment card data to convert the data to cash.
"On average, websites are compromised for 5.5 months before they are notified or detect something amiss."
It’s usually at this “cash out” phase that the websites are alerted, via their bank, that they have been hacked and are now facing forensic investigations, card brand liabilities, customer litigation, brand damage and potentially catastrophic trading disruption.
A regular scan using freely available technology like our WebScan tool could help them to avoid these issues by understanding that a few simple, yet critical security changes to their website could be the difference between becoming a victim of criminals and being safe and secure to continue doing good business.
When analysing the Magento statistics (being the leader in eCommerce sites and therefore present a larger potential impact to card data theft) across regions, we found the following regional market split:
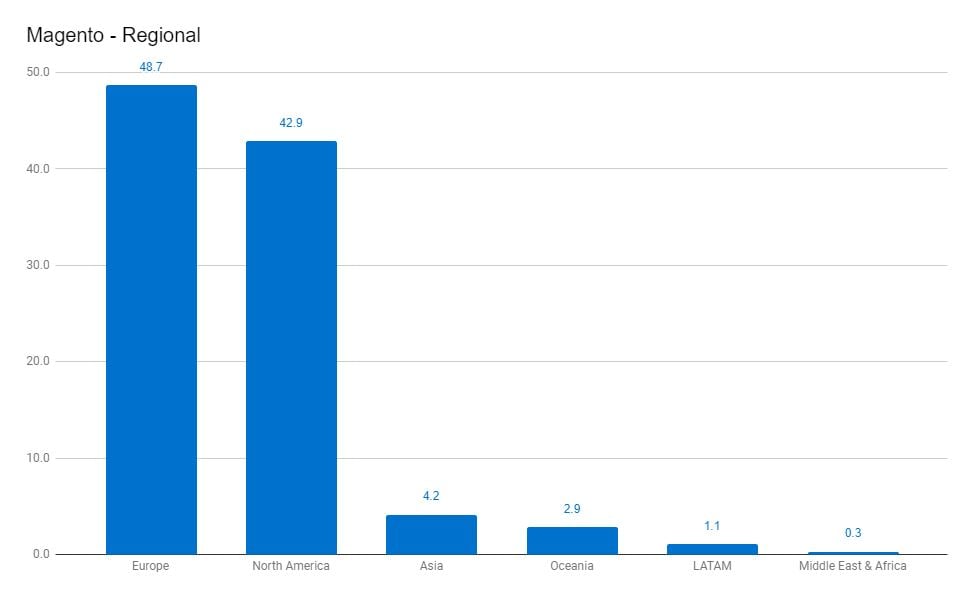
Europe: 48.7%
North America: 42.9%
Asia: 4.2%
Oceania: 2.9%
LATAM: 1.1%
Middle East and Africa: 0.3%
Drilling into the hacked Magento sites, this is the number of websites with payment card harvesting malware by region:
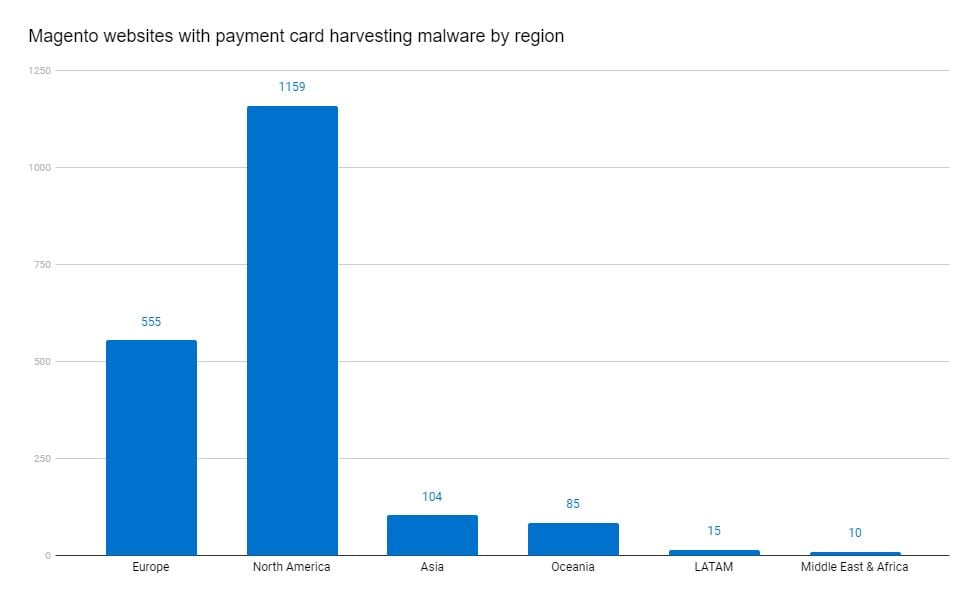
Europe: 555
North America: 1,159
Asia: 104
Oceania: 85
LATAM: 15
Middle East and Africa: 10
North American businesses make up 42.9% of the total Magento sites scanned globally; however, we found that 60.1% of the hacked Magento websites were from North America, with Europe containing 28.8%. Fairly consistently across the regions, we found that around 1.5% of the regional total number of Magento sites were hacked, with Europe being a low outlier with only 0.63% of Magento sites hacked.
"We found that 60% of the hacked Magento websites were from North America."
Malware
In reviewing and analysing the malware being used to harvest the payment card data, we distilled the malware into the following categories:
|
Malware |
Total |
|
Grelos JavaScript card data harvesting code. |
300 |
|
JavaScript malicious code injector (often used to deliver card harvesting malware). |
282 |
|
Javascript harvesting code that exfiltrates card data to a malicious domain when it is on the checkout page (multiple variants). |
277 |
|
Card harvesting malware that uses a polymorphic loader to mask itself. |
61 |
|
Guruincsite JavaScript Harvester. |
23 |
|
Supply Chain Attack - Harvesting Code. Malicious code injected into legitimate third-party code in order to infect its customers. |
12 |
|
JavaScript harvester which uses an image tag to exfiltrate data. |
5 |
|
Encoded Malicious Domain. A reference to an encoded known malicious domain was detected. The domain can be used to inject malware onto your website or to extract information stolen from legitimate users. (not strictly malware, but known to be bad) |
7 |
|
Cryptojacking Malware. The miner uses visitors computers CPU resources to mine digital cryptocurrency and send the resulting profits back to the attackers account. |
3 |
Summary
From our analysis over the last few months, it’s clear that Magento continues to be the focus of criminals. However, we have also begun to see an increase in supply chain attacks, which can affect multiple platforms including the SaaS platforms such as Shopify, BigCommerce and Magento Enterprise Cloud Edition.
"We have begun to see an increase in supply chain attacks, which can affect multiple platforms including SaaS platforms such as Shopify, BigCommerce and Magento Enterprise Cloud Edition."
How do we, as an industry defend against these criminals?
Through 10 years of forensic investigations on hacked eCommerce businesses, we’ve found that most breaches are not a result of extremely clever cyber criminal techniques. Rather, they are the result of basic security issues that have been overlooked by the website owner/web developers - the most common being a failure to deploy software patches quickly. A lot has been written on how to secure a website - check out our 11 steps to Improve your Website Security article.
The problem right now is that nearly 1,000 Magento sites in our research are currently hacked and losing their customer data - and they most likely don’t have a clue that they are being robbed. So what do we do?
How do we notify these websites that they are hacked?
Unfortunately, getting the message out to the hacked online businesses is challenging - an unsolicited call rarely gets the right level of attention and the vast majority of these businesses do not have a relationship with Foregenix. We've tried this with very limited success. We don’t believe in naming and shaming these victims either - no matter how alluring the short term fame, PR and social media followers may be, we don’t feel it is a responsible approach to take for the affected businesses.
Who does have the ability to help these businesses?
Well, we need to look at common denominators - in the payment world, the common denominators are the card brands, particularly Visa, American Express and Mastercard. However, the card brands do not have a direct relationship with online businesses - so who does?
Each online business will have an acquiring bank to process their transactions and we believe that, in partnership with the acquiring banks, we could help the affected eCommerce businesses to:
- Understand why their websites have been hacked
- Provide guidance on how to secure their websites
- Monitor the security of their online businesses going forward to help them prevent vulnerabilities from becoming compromises of their customer data
Our industry is built on trust, verified trust. On this basis, we would never publish “The List” of hacked websites for the world to see - we believe that through collaboration with the stewards of the industry - the card brands, the acquiring banks, payment processors - perhaps even the Magento community itself - we can very quickly help these businesses.
What can you do to protect your business?
To check your website for free, please visit: https://webscan.foregenix.com/
If you're a Magento Web Developer and you're interested in learning about how to secure your client sites, please join us on our upcoming webinar: Top Security Tips for Magento Web Developers.
To enroll in a free monthly scan of your website, you can sign up here: https://portal.foregenix.com/signup/fgx-web-free
More proactively minded?
If you wanted to get more proactive, we offer a range of service tiers to protect your eCommerce business.
Let’s get proactive and together we can prevent these fraudsters from stealing from your business.
Subscribe to our Blog

Benjamin Hosack
Benj Hosack is a Director and co-Founder of Foregenix Limited. Foregenix is a specialist information security business delivering services in Forensics, PCI DSS, PCI P2PE, PA-DSS and information security solutions within the Payment Card Industry. Our technologies are designed to simplify security and PCI Compliance. Specialties: Cardholder Data Discovery - defining and reducing PCI DSS Scope / PA-DSS / PCI DSS / P2PE / Account Data Compromise Investigations. We are specialists in the Payment Card Industry and work with all types of companies in the payment chain (Acquiring banks, Processors, hosting providers, web designers, merchants, systems integrators etc).
See All Articles